What Is A Firewall Standard Subscription Service
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical back up.
Azure Firewall Standard features
Azure Firewall Standard is a managed, cloud-based network security service that protects your Azure Virtual Network resources.
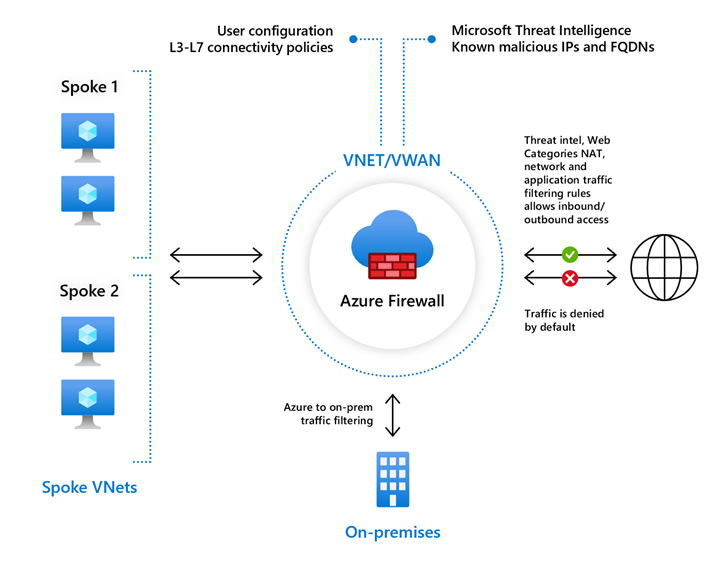
Azure Firewall includes the following features:
- Built-in loftier availability
- Availability Zones
- Unrestricted deject scalability
- Application FQDN filtering rules
- Network traffic filtering rules
- FQDN tags
- Service tags
- Threat intelligence
- DNS proxy
- Custom DNS
- FQDN in network rules
- Deployment without public IP address in Forced Tunnel Fashion
- Outbound SNAT support
- Inbound DNAT support
- Multiple public IP addresses
- Azure Monitor logging
- Forced tunneling
- Web categories
- Certifications
Congenital-in loftier availability
High availability is built in, and then no extra load balancers are required and there'south nothing you need to configure.
Availability Zones
Azure Firewall can be configured during deployment to span multiple Availability Zones for increased availability. With Availability Zones, your availability increases to 99.99% uptime. For more than data, see the Azure Firewall Service Level Agreement (SLA). The 99.99% uptime SLA is offered when two or more Availability Zones are selected.
Yous can besides associate Azure Firewall to a specific zone just for proximity reasons, using the service standard 99.95% SLA.
There's no additional toll for a firewall deployed in an Availability Zone. Nevertheless, there are added costs for inbound and outbound data transfers associated with Availability Zones. For more information, come across Bandwidth pricing details.
Azure Firewall Availability Zones are available in regions that back up Availability Zones. For more than information, meet Regions that back up Availability Zones in Azure
Annotation
Availability Zones can only be configured during deployment. You can't configure an existing firewall to include Availability Zones.
For more information about Availability Zones, see Regions and Availability Zones in Azure.
Unrestricted cloud scalability
Azure Firewall tin can scale out as much equally you lot need to arrange changing network traffic flows, so you don't need to budget for your height traffic.
Application FQDN filtering rules
Y'all can limit outbound HTTP/Southward traffic or Azure SQL traffic to a specified list of fully qualified domain names (FQDN) including wild cards. This feature doesn't require TLS termination.
Network traffic filtering rules
You lot can centrally create allow or deny network filtering rules past source and destination IP address, port, and protocol. Azure Firewall is fully stateful, so it can distinguish legitimate packets for unlike types of connections. Rules are enforced and logged across multiple subscriptions and virtual networks.
Azure Firewall supports stateful filtering of Layer 3 and Layer 4 network protocols. Layer 3 IP protocols tin be filtered past selecting Whatever protocol in the Network rule and select the wild-card * for the port.
FQDN tags make it easy for you to let well-known Azure service network traffic through your firewall. For example, say you want to allow Windows Update network traffic through your firewall. Y'all create an awarding dominion and include the Windows Update tag. Now network traffic from Windows Update can flow through your firewall.
A service tag represents a grouping of IP accost prefixes to assist minimize complexity for security rule creation. You tin can't create your own service tag, nor specify which IP addresses are included inside a tag. Microsoft manages the accost prefixes encompassed past the service tag, and automatically updates the service tag every bit addresses change.
Threat intelligence
Threat intelligence-based filtering can be enabled for your firewall to alert and deny traffic from/to known malicious IP addresses and domains. The IP addresses and domains are sourced from the Microsoft Threat Intelligence feed.
DNS proxy
With DNS proxy enabled, Azure Firewall can process and forrard DNS queries from a Virtual Network(s) to your desired DNS server. This functionality is crucial and required to have reliable FQDN filtering in network rules. You lot can enable DNS proxy in Azure Firewall and Firewall Policy settings. To learn more about DNS proxy, see Azure Firewall DNS settings.
Custom DNS
Custom DNS allows yous to configure Azure Firewall to use your own DNS server, while ensuring the firewall outbound dependencies are withal resolved with Azure DNS. You may configure a single DNS server or multiple servers in Azure Firewall and Firewall Policy DNS settings. Learn more about Custom DNS, meet Azure Firewall DNS settings.
Azure Firewall tin can also resolve names using Azure Private DNS. The virtual network where the Azure Firewall resides must be linked to the Azure Private Zone. To learn more, see Using Azure Firewall equally DNS Forwarder with Private Link.
FQDN in network rules
You can use fully qualified domain names (FQDNs) in network rules based on DNS resolution in Azure Firewall and Firewall Policy.
The specified FQDNs in your dominion collections are translated to IP addresses based on your firewall DNS settings. This capability allows you to filter outbound traffic using FQDNs with any TCP/UDP protocol (including NTP, SSH, RDP, and more). Equally this capability is based on DNS resolution, information technology is highly recommended you enable the DNS proxy to ensure proper noun resolution is consistent with your protected virtual machines and firewall.
Deploy Azure Firewall without public IP address in Forced Tunnel mode
The Azure Firewall service requires a public IP accost for operational purposes. While secure, some deployments prefer not to betrayal a public IP address direct to the Internet.
In such cases, you can deploy Azure Firewall in Forced Tunnel style. This configuration creates a management NIC which is used by Azure Firewall for its operations. The Tenant Datapath network can be configured without a public IP accost, and Net traffic tin can be forced tunneled to another firewall or completely blocked.
Forced Tunnel mode cannot be configured at run time. You can either redeploy the Firewall or use the finish and beginning facility to reconfigure an existing Azure Firewall in Forced Tunnel style. Firewalls deployed in Secure Hubs are always deployed in Forced Tunnel way.
Outbound SNAT support
All outbound virtual network traffic IP addresses are translated to the Azure Firewall public IP (Source Network Address Translation). Y'all can place and allow traffic originating from your virtual network to remote Net destinations. Azure Firewall doesn't SNAT when the destination IP is a private IP range per IANA RFC 1918.
If your organization uses a public IP accost range for individual networks, Azure Firewall will SNAT the traffic to one of the firewall private IP addresses in AzureFirewallSubnet. Y'all can configure Azure Firewall to non SNAT your public IP accost range. For more information, run across Azure Firewall SNAT private IP address ranges.
You can monitor SNAT port utilization in Azure Firewall metrics. Learn more and see our recommendation on SNAT port utilization in our firewall logs and metrics documentation.
Entering DNAT support
Inbound Cyberspace network traffic to your firewall public IP address is translated (Destination Network Address Translation) and filtered to the individual IP addresses on your virtual networks.
Multiple public IP addresses
You can acquaintance multiple public IP addresses (up to 250) with your firewall.
This enables the following scenarios:
- DNAT - You tin can interpret multiple standard port instances to your backend servers. For example, if y'all take 2 public IP addresses, you lot can translate TCP port 3389 (RDP) for both IP addresses.
- SNAT - More ports are bachelor for outbound SNAT connections, reducing the potential for SNAT port exhaustion. At this time, Azure Firewall randomly selects the source public IP address to use for a connection. If you lot have any downstream filtering on your network, you demand to allow all public IP addresses associated with your firewall. Consider using a public IP address prefix to simplify this configuration.
Azure Monitor logging
All events are integrated with Azure Monitor, allowing you to archive logs to a storage account, stream events to your Effect Hub, or send them to Azure Monitor logs. For Azure Monitor log samples, come across Azure Monitor logs for Azure Firewall.
For more information, see Tutorial: Monitor Azure Firewall logs and metrics.
Azure Firewall Workbook provides a flexible canvas for Azure Firewall information assay. You tin apply it to create rich visual reports inside the Azure portal. For more information, see Monitor logs using Azure Firewall Workbook.
Forced tunneling
Y'all can configure Azure Firewall to route all Internet-leap traffic to a designated side by side hop instead of going direct to the Internet. For example, you may take an on-premises edge firewall or other network virtual apparatus (NVA) to process network traffic before it's passed to the Net. For more than information, see Azure Firewall forced tunneling.
Web categories
Web categories lets administrators allow or deny user access to web site categories such as gambling websites, social media websites, and others. Web categories are included in Azure Firewall Standard, but information technology'southward more fine-tuned in Azure Firewall Premium. As opposed to the Spider web categories capability in the Standard SKU that matches the category based on an FQDN, the Premium SKU matches the category according to the entire URL for both HTTP and HTTPS traffic. For more information nearly Azure Firewall Premium, meet Azure Firewall Premium features.
For case, if Azure Firewall intercepts an HTTPS asking for world wide web.google.com/news, the following categorization is expected:
-
Firewall Standard – simply the FQDN part volition exist examined, so
www.google.comwill be categorized every bit Search Engine. -
Firewall Premium – the complete URL will be examined, so
world wide web.google.com/newsvolition be categorized as News.
The categories are organized based on severity under Liability, Loftier-Bandwidth, Business Utilize, Productivity Loss, General Surfing, and Uncategorized.
Category exceptions
You can create exceptions to your web category rules. Create a separate allow or deny dominion collection with a higher priority within the rule collection group. For example, yous can configure a rule collection that allows www.linkedin.com with priority 100, with a rule drove that denies Social networking with priority 200. This creates the exception for the pre-defined Social networking web category.
Certifications
Azure Firewall is Payment Card Industry (PCI), Service System Controls (SOC), International Organization for Standardization (ISO), and ICSA Labs compliant. For more than information, meet Azure Firewall compliance certifications.
Next steps
- Azure Firewall Premium features
Feedback
Submit and view feedback for
Source: https://docs.microsoft.com/en-us/azure/firewall/features
Posted by: cervantezglanking.blogspot.com


0 Response to "What Is A Firewall Standard Subscription Service"
Post a Comment